Passware offers a free tool, Encryption Analyzer, that scans computers and network drives, finds encrypted files and hard disk images, and lists them along with other related information, such as encryption type, password recovery complexity, and MD5 hash.
This module is also integrated into all editions of Passware Kit to allow for immediate decryption of discovered items.
The following are 5 tips for the most effective analysis of encrypted electronic evidence.
Tip 1: Sort files according to their decryption complexity
Since many users tend to rely on the same or similar passwords to protect various types of files, we recommend starting the password recovery process with the files that have the weakest encryption (such as older versions of MS Office and PDF) in order to discover passwords. Passware Kit recovers many types of passwords instantly and automatically saves them to its default dictionary. When it comes to other files with stronger encryption, Passware Kit first checks previously recovered passwords and some variants before applying more laborious password recovery strategies. This approach increases the chances of finding passwords for well-encrypted files, such as archives or keychains.
After Encryption Analyzer has listed the encrypted items, you can sort them according to their decryption complexity by clicking the “Recovery Complexity” column:
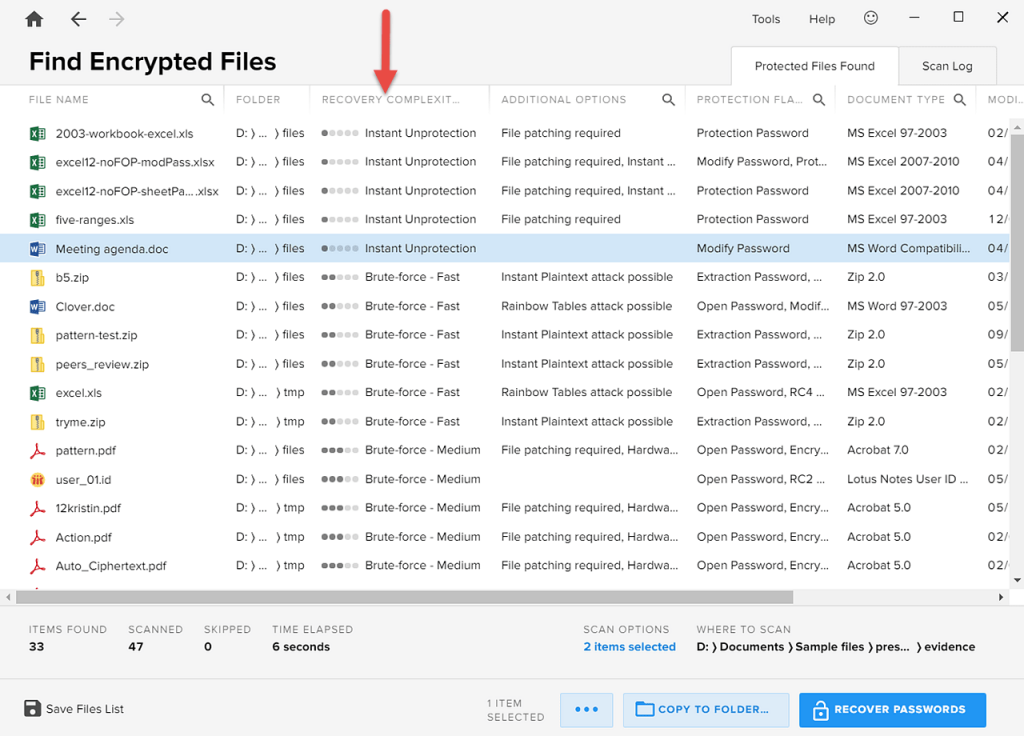
The files are now sorted from “Instant Unprotection” all the way through to the “Brute-force – Slow” strategy.
Tip 2: Initiate batch password recovery directly from Encryption Analyzer
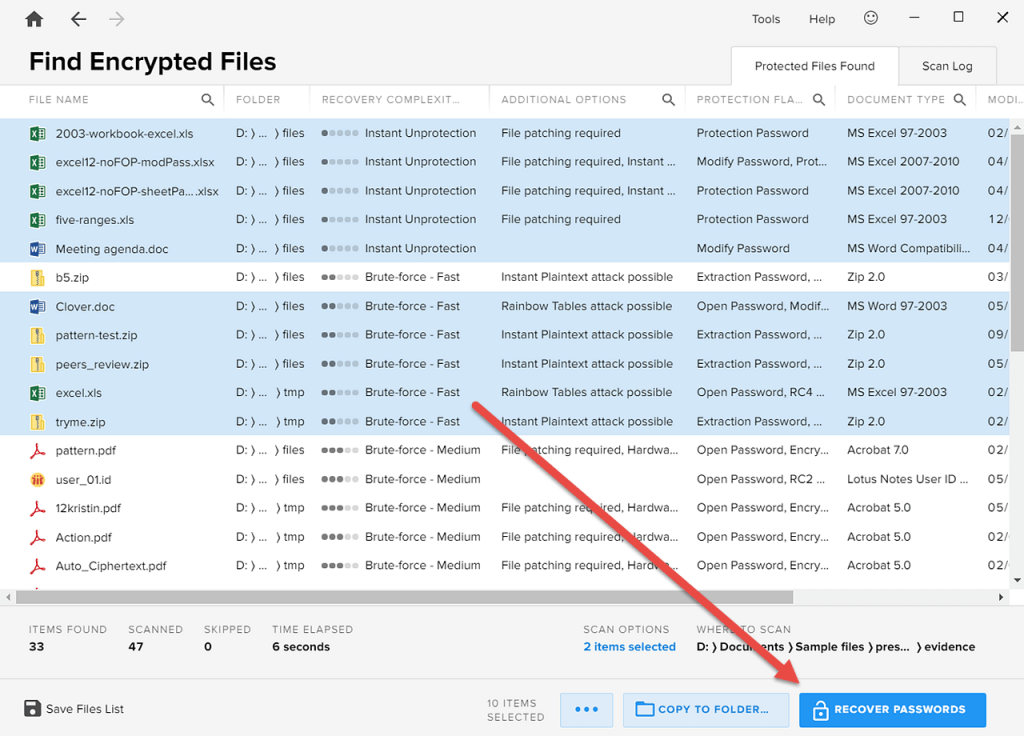
Once you have sorted the list of encrypted items, you can start the password recovery process directly from Encryption Analyzer (provided that Passware Kit is installed). Select the files that you want to decrypt and click the “Recover Passwords” button, which initiates a batch password recovery process for each of the files.
Bearing in mind Tip 1, first select files with “Instant Unprotection” and “Brute-force – Fast” flags:
Tip 3: Use incremental search to work with particular files
After Encryption Analyzer has listed the encrypted evidence, the incremental search option can be used to narrow down the set of files to work with. This way, you can find and display files by name, encryption type, or decryption complexity.
It can be useful to filter the encrypted files based on the following parameters:
- files that support hardware acceleration,
- files that support memory analysis or rainbow table attacks,
- specific document types, such as MS Excel.
To search for a particular parameter, simply click the magnifier icon beside the column in which you would like to search and type the keyword. Typing “rainbow” in the “Additional Options” column, for example, produces a list of files that can be decrypted using rainbow tables:
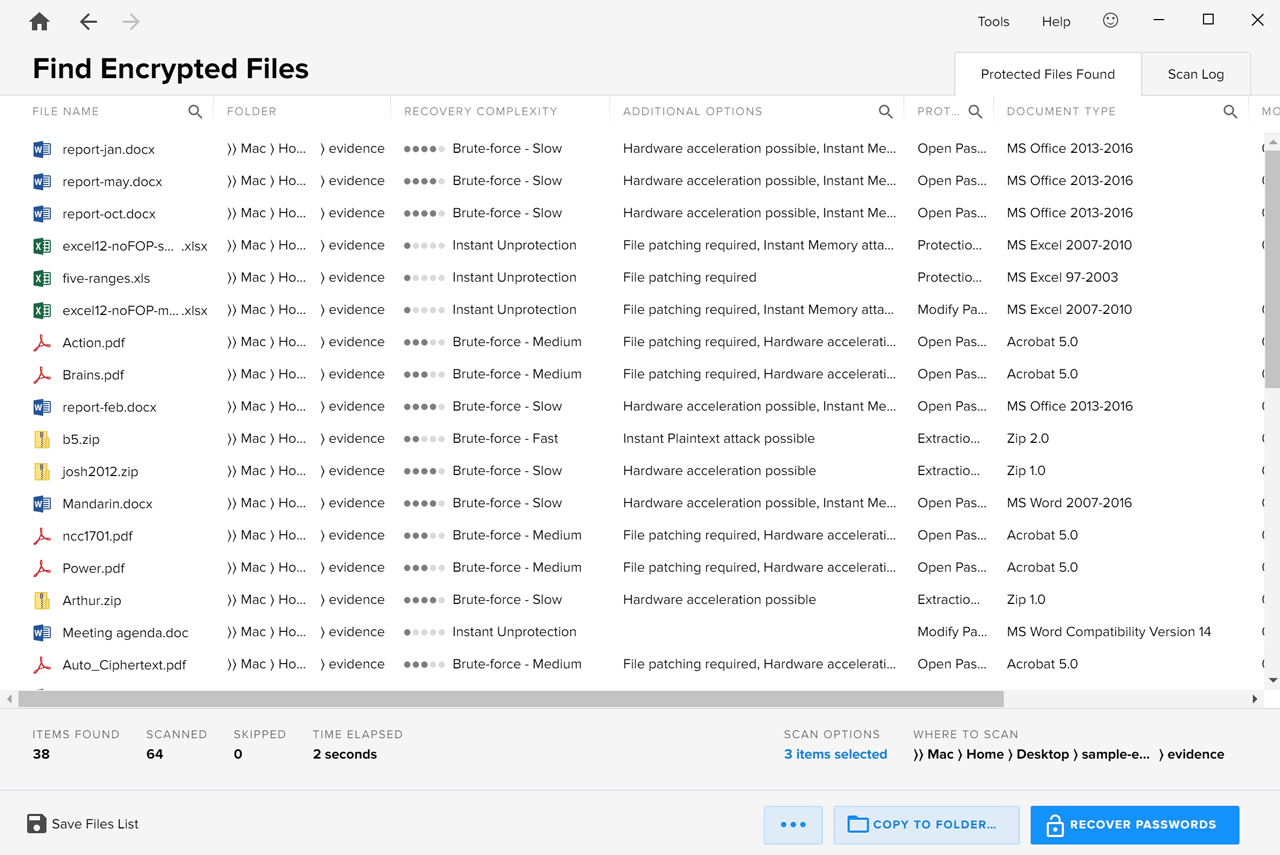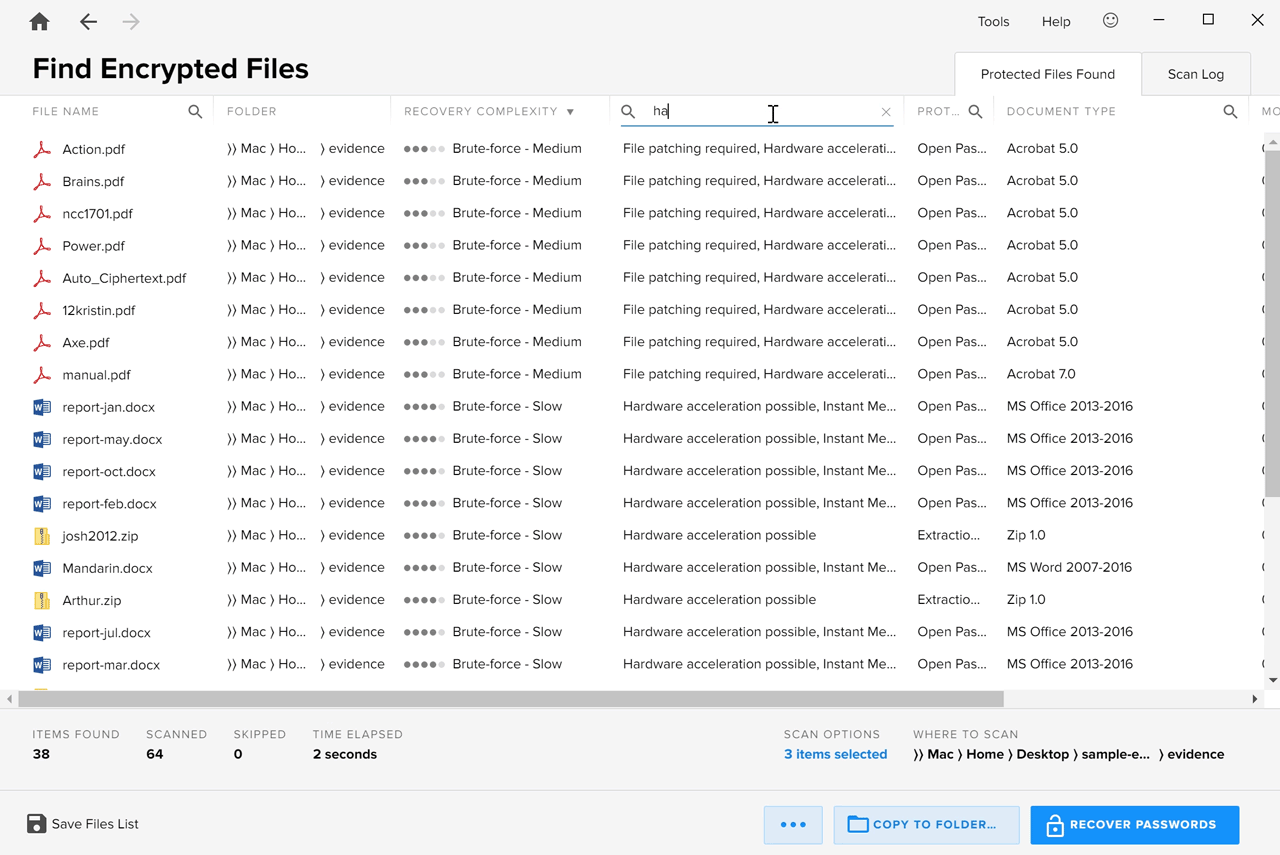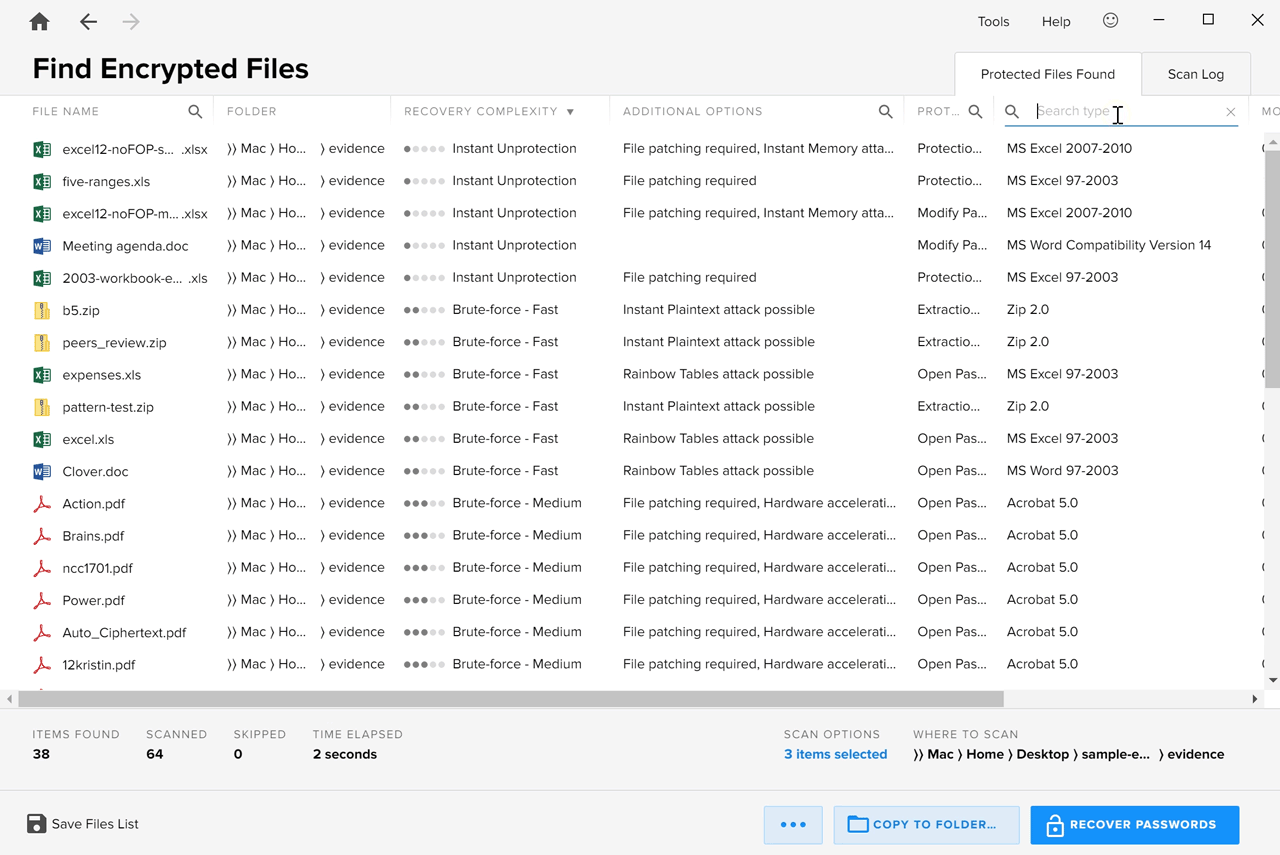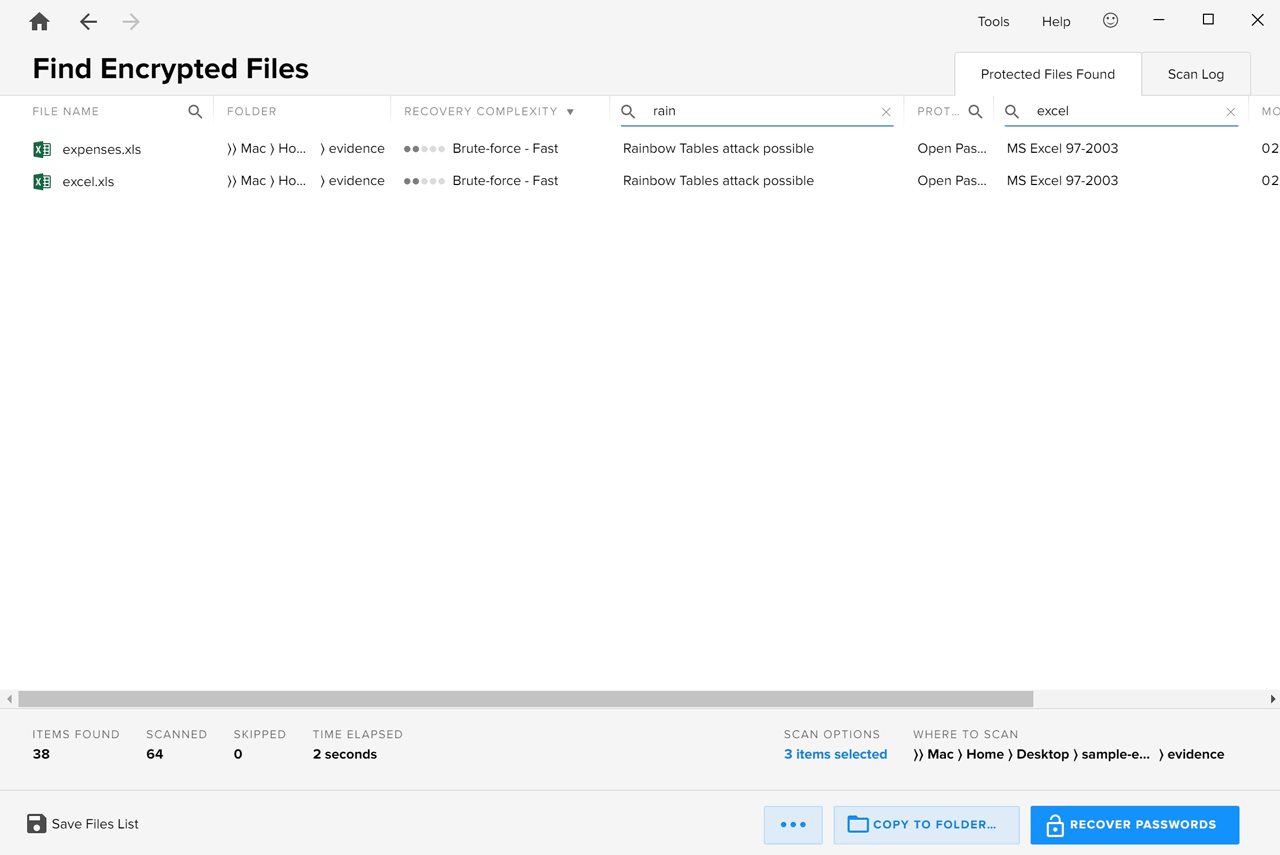
To clear the filter results, click the [x] icon.
The filtered files can be easily copied to a separate folder for further analysis or immediate password recovery by clicking the “Copy to Folder” button.
Tip 4: Export and import scan results
Passware Kit Forensic includes a portable USB version that can be run on a suspect’s computer without installation. You can use this portable version directly on a target PC to identify all of the encrypted items and then export the results along with any files of interest to your work computer or a more powerful system in order to perform batch decryption.
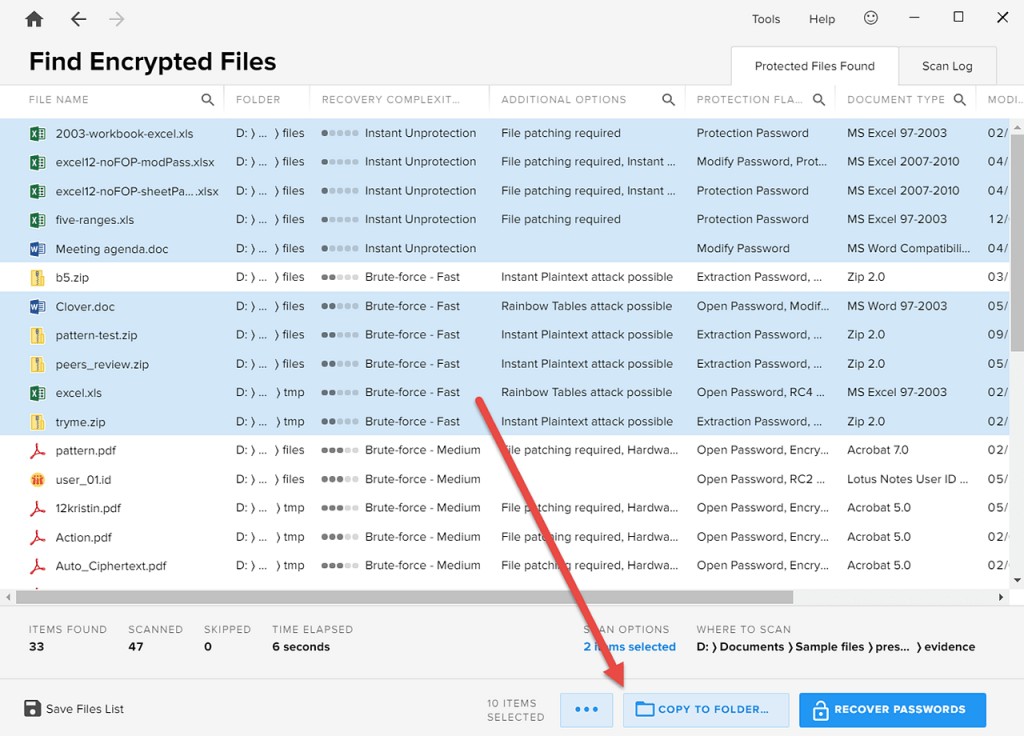
To save the scan results, click the “Save Files List” icon. Again, you can use the “Copy to Folder” to copy the selected files (e.g. to an external drive) for further decryption; just click the button:
Tip 5: Find encrypted hard disk images
With Encryption Analyzer, you can also find images of hard disks encrypted with TrueCrypt, VeraCrypt, PGP, BitLocker, LUKS, etc.
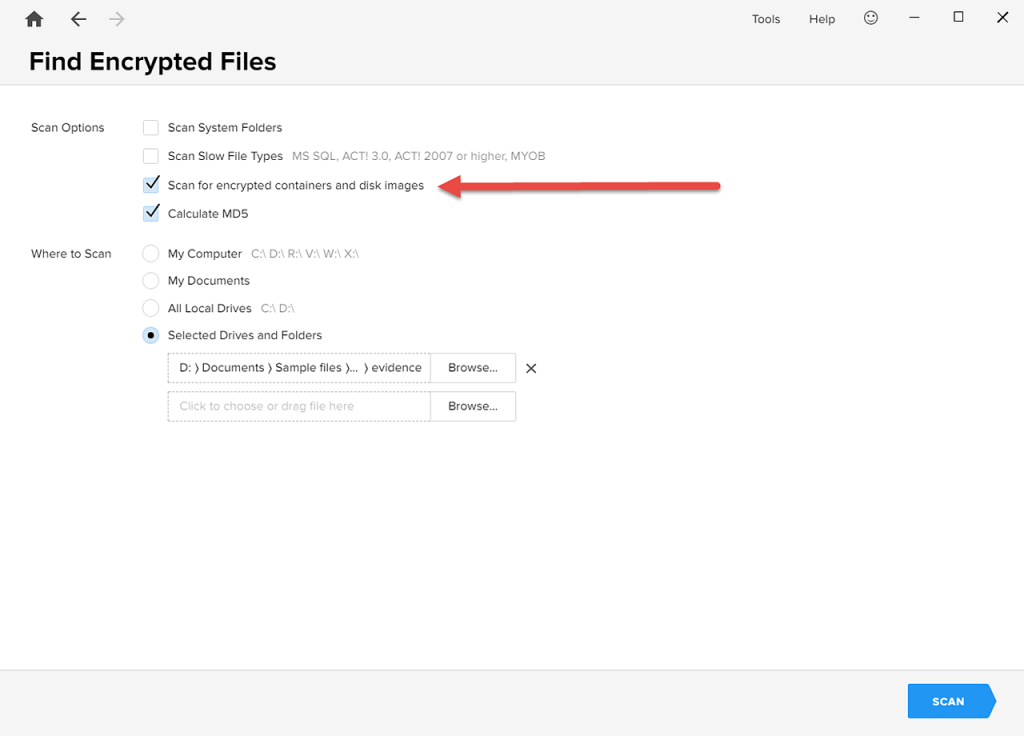
Make sure that the option “Scan for encrypted containers and disk images” is enabled when you begin:
After Encryption Analyzer has displayed the scan results, select the disk image and click “Recover Passwords”:
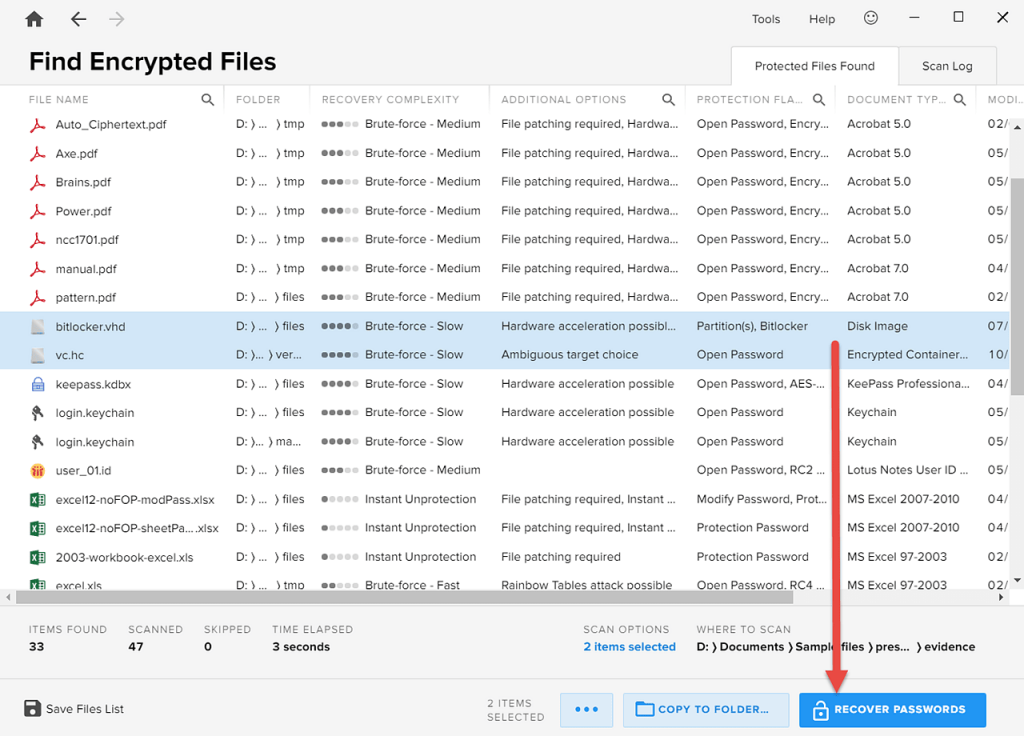
Passware Kit then asks you to choose the disk decryption option based on what you know about the hard disk.
Summary
For the most complete analysis of encrypted electronic evidence, Encryption Analyzer offers five powerful options: sorting by decryption complexity, immediate batch password recovery processes, incremental searching on lists of encrypted items, exporting and importing results, and finding encrypted hard disk images.