The Microsoft Windows operating system stores passwords and other login data for the installed applications on a system disk in the user profile directory, as well as in a hierarchical Windows registry database. By acquiring this database from a target system, computer forensics gain a source of invaluable data essential for an investigation.
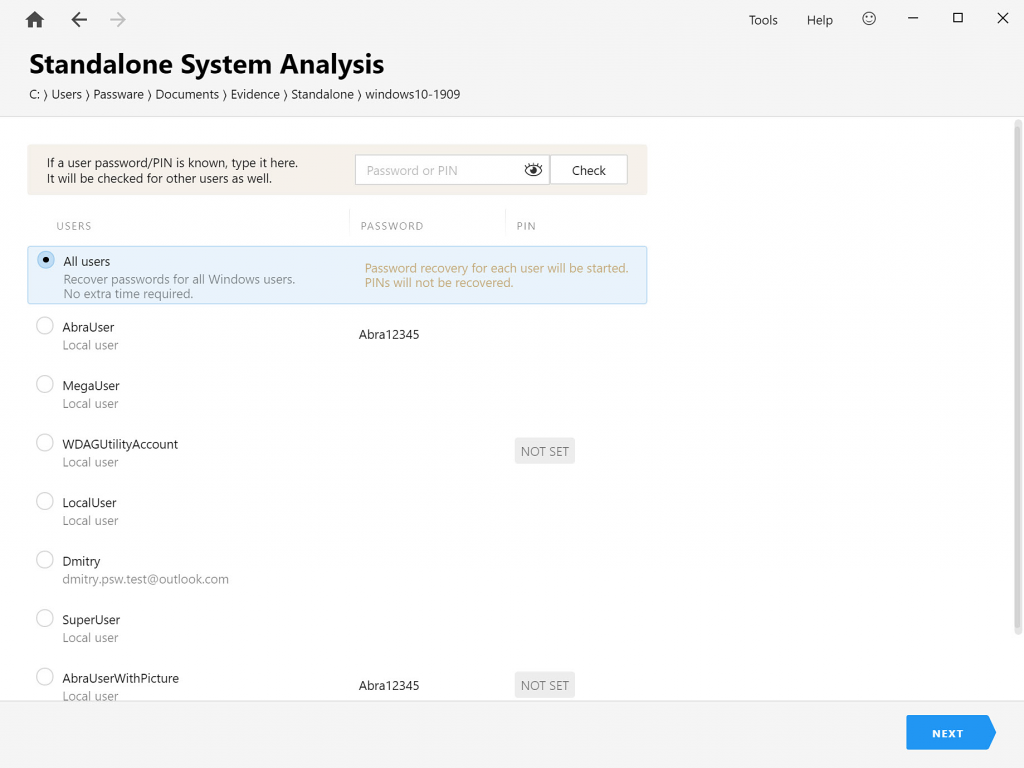
An examiner can use a set of external registry hives and user profile files acquired from the target computer or its disk image for password recovery and electronic evidence discovery.
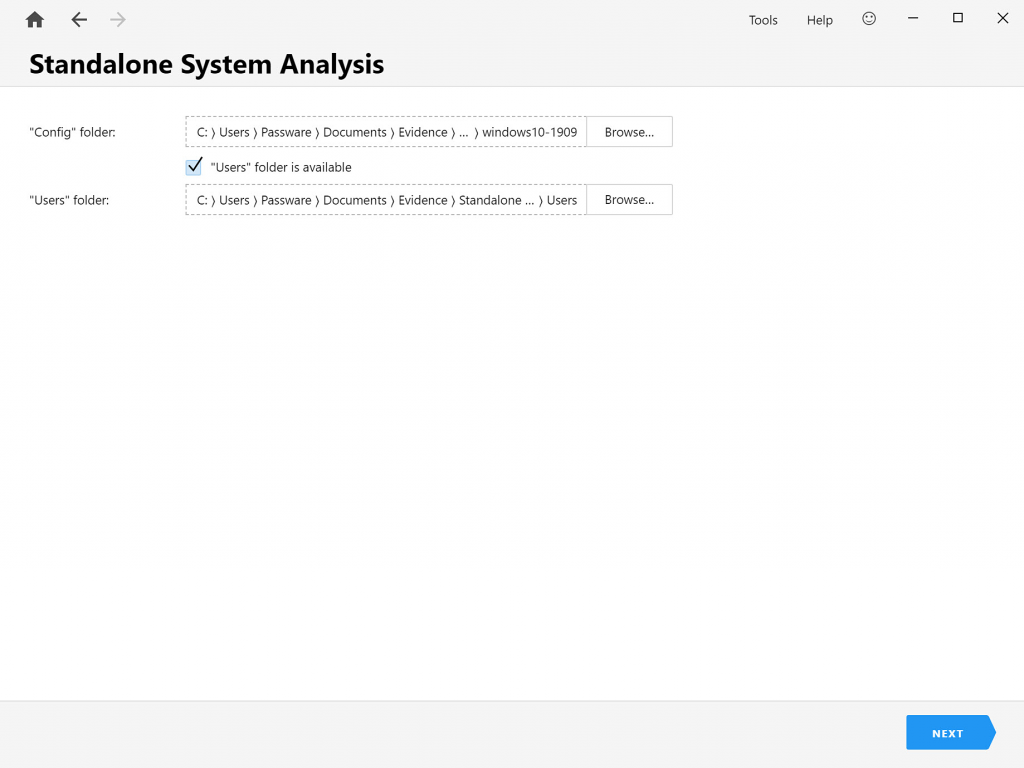
The “Standalone System” option, which is used to extract logins and passwords, is available in the Forensic edition of the Passware Kit only.
Registry files required
Registry files are locked by the operating system. For this reason, they should be extracted from a hard disk image of the target computer by using accepted forensic practices or software that provides direct access to the hard disk, such as DiskInternals Linux Reader.
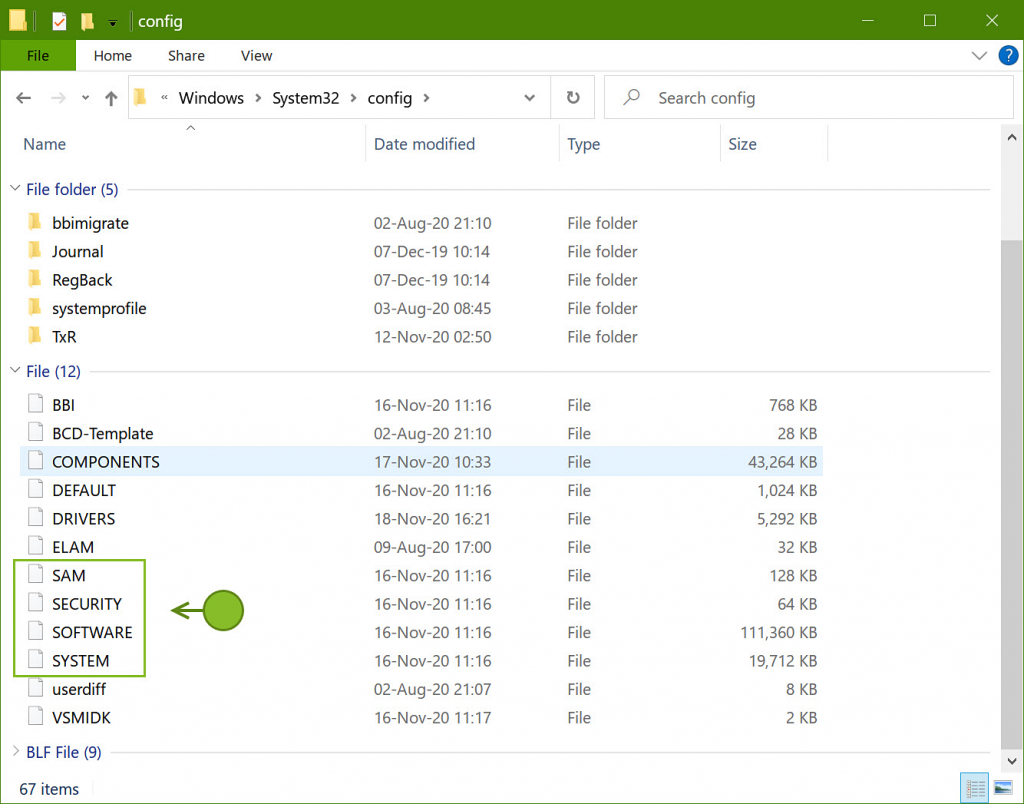
Windows user passwords are stored in the Security Accounts Manager (SAM) file in a hashed format (in LM hash and NTLM hash). To recover these passwords, we also need the files SECURITY and SYSTEM. All of them are located at: “Windows\system32\config”.
Password recovery for Windows hashes is a brute-force process, which can be accelerated with GPU and distributed computing. An average speed on a single NVIDIA 2080ti is 19 billion passwords per second. Rainbow Tables can also be used to decrypt the hashes and recover the passwords. To recover a Windows PIN, additional folders from the “C:\Windows\” directory are required, such as:
– Windows\ServiceProfiles,
– Windows\System32\config\systemprofile, and
– Windows\System32\Microsoft\Protect.
After the Windows user password or PIN is recovered, Passware Kit can instantly extract passwords for websites, network connections, and email accounts from the “Users” folder located in the root of the C: drive by default.
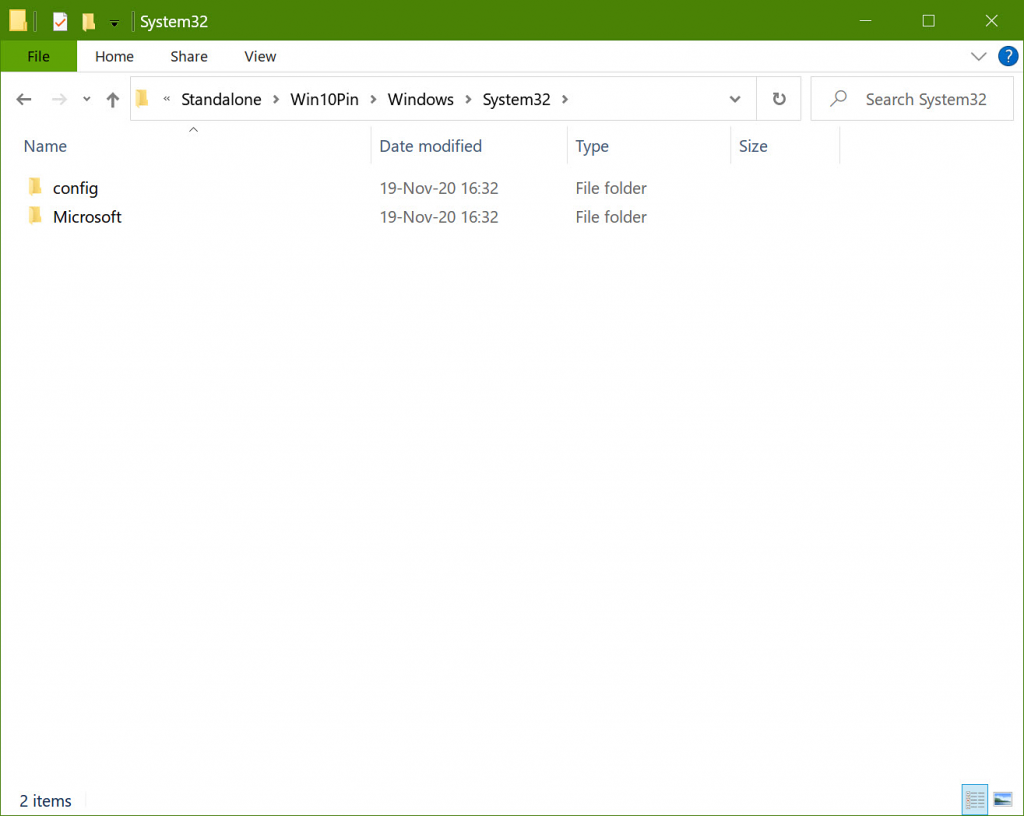
For successful password extraction, the structure of the target registry files should be saved: when specifying a path to the folder “config” in Passware Kit, make sure that the folder “Microsoft” is also located together with “config”, just as it appears in the “system32” folder in Windows.
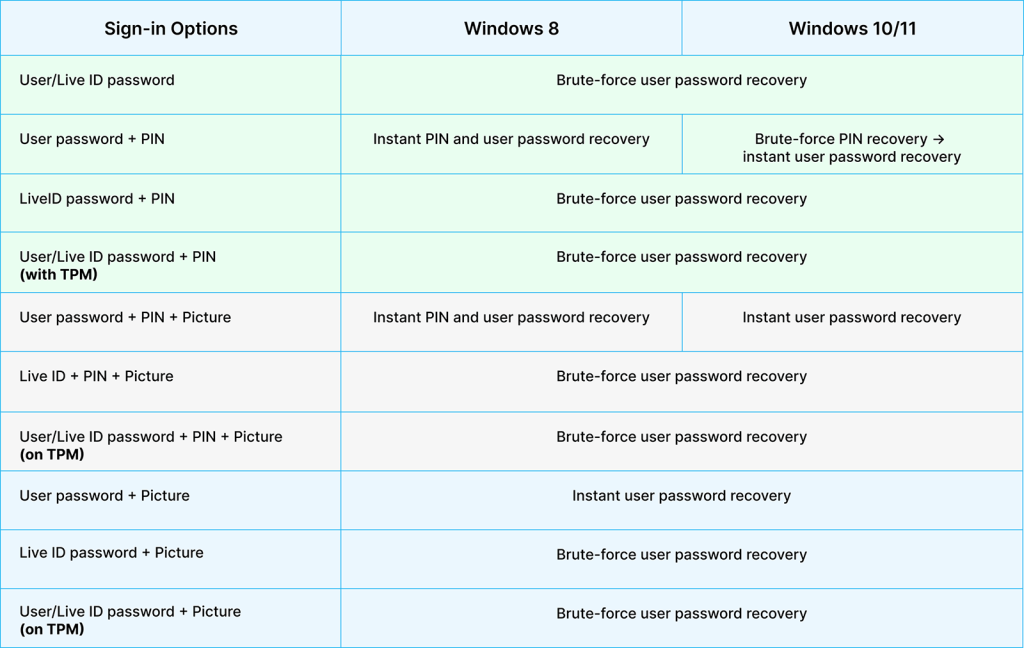
Windows user password recovery depending on the sign-in options
For Windows 7 and earlier systems, a Windows user password can be recovered using either a brute-force approach or a Rainbow Tables attack.
Windows systems starting from Windows 8 can be protected with PIN and Picture password in addition to the regular user password (Windows Hello options). In fact, these additional sign-in options undermine Windows security and allow instant recovery of the user password. Here’s what Passware Kit can do to recover user passwords depending on the sign-in options.
*For Windows 10/11, in case a PIN needs to be recovered, Passware Kit first detects whether it is fully numerical (default settings) or not. If the PIN contains numbers only, Passware Kit automatically recovers it with the predefined settings. If the PIN is a combination of letters and numbers, Passware Kit asks a user to customize the brute-force settings.
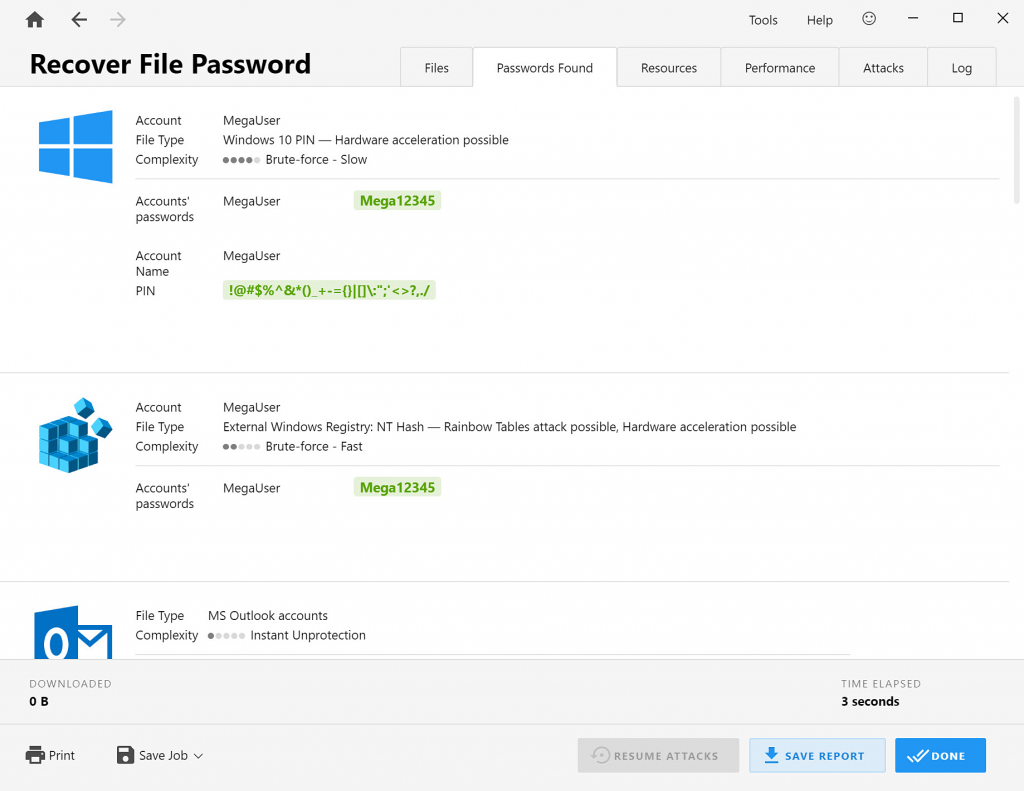
After Passware Kit recovers the PIN or password for some Windows user, it immediately checks it for other Windows users.
Extraction of passwords and data after a user password is recovered
After a Windows user password is recovered, Passware Kit proceeds to instant extraction of passwords and other data stored in registry for this particular user. It is possible to recover passwords for MS Outlook, Outlook Express, and Mozilla Thunderbird email clients, website passwords saved in web browsers (Internet Explorer 6-11, Google Chrome, Mozilla Firefox, Safari, Opera, Opera GX and Crypto, Microsoft Edge), and network connections passwords (Wi-Fi and Windows network credentials):
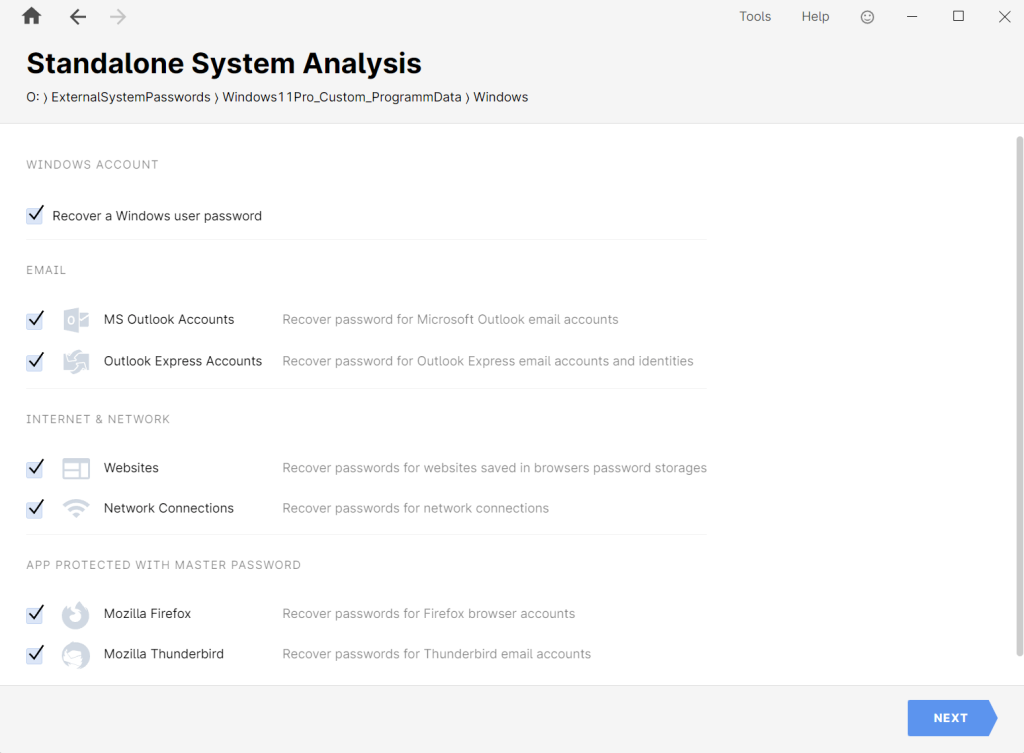
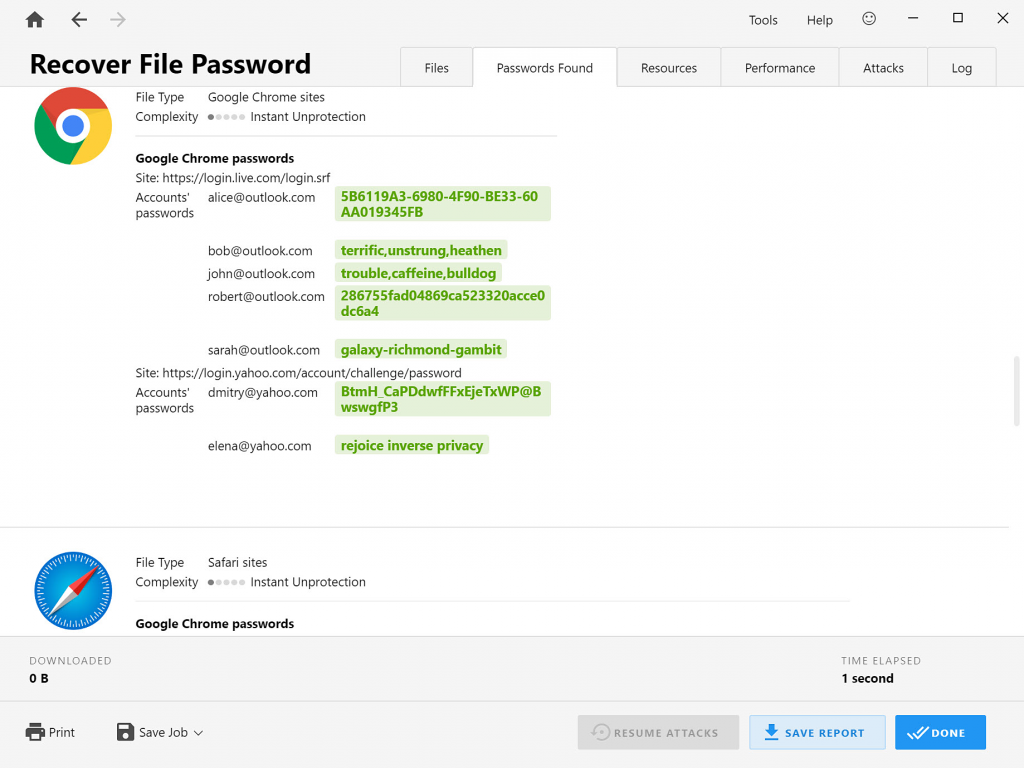
All the recovered passwords are saved in the Passware Kit “Previous Passwords” dictionary to be reused for other password-protected items, and can also be saved in CSV reports.