We are celebrating 20 years of Passware with the biggest update to our flagship product yet, Passware Kit Forensic 2018 v1.
From the all-new UI and faster GPU-accelerated password recovery to one-step memory analysis, we have improved the efficiency of our decryption tool, which has earned the trust of forensic and security professionals worldwide.
The new version of Passware Kit Forensic features a redesigned user interface and the capability to decrypt Apple File System (APFS) disks and macOS High Sierra Keychains.
Memory analysis now works as a one-step streamlined process for multiple evidence types and encryption artifacts, while optimized algorithms provide faster password recovery for TrueCrypt, Android, Zip, and many other types of files.
Passware Kit 2018 v1 can be used side-by-side with Passware Kit 2017. You can install the new version on a computer that is already running an earlier Passware Kit version.
What’s New
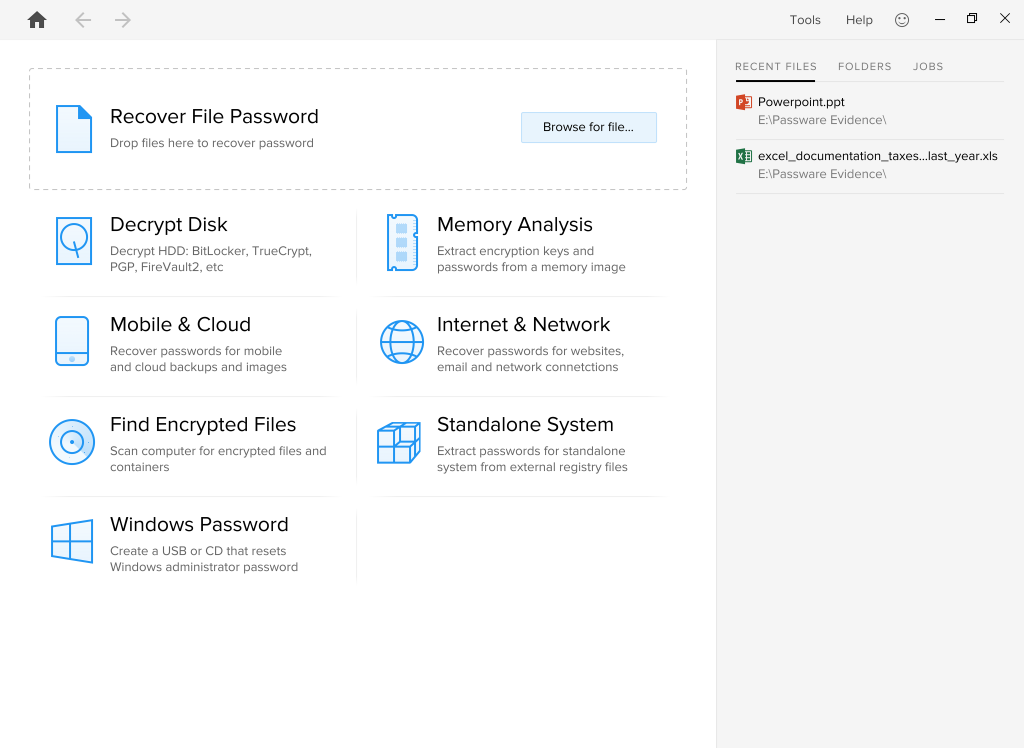
All-new UI
A new UI for easy navigation and intuitive access to all of the application’s features.
Decryption of Apple File System (APFS) disks
Passware Kit now decrypts APFS disk images via live memory analysis and GPU-accelerated brute-force password recovery.
One-step memory analysis
Passware Kit now extracts multiple evidence types from memory images in a single streamlined process, from encryption keys and passwords to cloud authorization tokens.
Password recovery for macOS High Sierra Keychains
Password recovery for macOS High Sierra Keychains with subsequent data extraction.
Faster GPU-accelerated password recovery for TrueCrypt, VeraCrypt, and Zip
GPU-accelerated password recovery is now up to 250% faster for TrueCrypt and VeraCrypt drives and 150% faster for Zip archives.
Improved performance for Android, Apple Disk, Zip, RAR, LUKS, OpenDocument, etc.
Passware Kit features code optimizations that allow faster password recovery for the following file types: Android backup, Android physical Image, Apple Disk image, FileVault2 image, iTunes backup, RAR 5, iWork’ 09, OpenDocument, Keychain, WPA, Zip AES, and LUKS image.
Keyboard mistypes modifier
A new modifier for password recovery attacks mimics keyboard mistypes so that each password character is replaced with all of the adjacent keys on the keyboard.
For example, if the “Keyboard mistypes” modifier is applied to the first character of the password “goal”, it generates the passwords “roal”, “toal”, “yoal”, “hoal”, “noal”, “boal”, “voal”, “foal”, and “goal” itself.
Quick-start guide
The new quick-start guide is a hands-on tutorial that walks you through the basic tasks of detecting and decrypting encrypted electronic evidence.
New dictionary
A new dictionary with over 2.5 billions passwords compiled from recent passwords leaks is now available for download from Passware Account. Leveraging this extensive wordlist greatly increases the chances of recovering even complex passwords.
Feedback tool
Passware is committed to making the best decryption tools for forensic examiners and security professionals.
Help us make Passware Kit better! Please use the feedback tool in the upper-right corner of Passware Kit to share your suggestions, feature requests, or problems.
Passware Kit Business and Passware Kit Forensic
customers only