VeraCrypt and the former TrueCrypt are two of the most challenging types of encryption to bypass with regard to their popularity as full disk encryption software.
Unlike Bitlocker encryption, TrueCrypt/VeraCrypt may encrypt their containers and volumes with multiple encryption keys (cascade encryption) applying the encryption types one by one. TrueCrypt and VeraCrypt do not store the information about the cascade, and once the encrypted volume is to be mounted, they search for the right cascade. Passware Kit extracts possible encryption keys from a memory image or a system hibernation file (hiberfil.sys) and searches for the right cascade type, just as TrueCrypt/VeraCrypt does. Then Passware Kit decrypts the given container. Additionally, beginning with version 1.24, VeraCrypt introduces a mechanism to encrypt master keys and cached passwords in RAM. Starting from version 2023 v1, Passware Kit supports this feature and decrypts the keys, providing instant access to the VeraCrypt volumes.
If the memory image is not available (it should be acquired when the target container or volume is mounted), only brute-force recovery of the original password is possible. The password recovery speed significantly depends on the number of encryption and hash algorithms that need to be checked, as well as the Personal Iterations Multiplier (PIM).
This article summarizes all the peculiarities of TrueCrypt/VeraCrypt encryption to help you understand how to make the decryption process more efficient.
TrueCrypt or VeraCrypt?
The main obstacle with TrueCrypt/VeraCrypt decryption is that password recovery for such containers does not have any effect if a user does not specify whether it is TrueCrypt or VeraCrypt. So, if you have a container to decrypt, the first task for you is to specify its application and encryption type, or at least to screen out irrelevant types using indirect indications.
For system partitions, Passware Kit analyzes the boot loader and recognizes whether the disk is TrueCrypt or VeraCrypt. Passware Kit also detects the system partitions of the GUID Partition Table (GPT) disks encrypted with VeraCrypt and further decrypts them. Since TrueCrypt does not support GPT, we can know for sure that this disk is VeraCrypt. Passware Kit Forensic detects it as VeraCrypt and starts an appropriate password recovery process.
For non-system partitions, it is impossible to tell which application was used. We recommend analyzing indirect indications, such as the target system registry and drivers, to deduce the disk type.
The registry key is eitherHKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\Windows\CurrentVersion\Uninstall\TrueCrypt
orHKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\Windows\CurrentVersion\Uninstall\VeraCrypt,
which indicates the application installed and assumes that it was used to create the target volume.
Encryption Hashes and Сascades
The TrueCrypt/VeraCrypt Random Number Generator uses a user-selected hash algorithm as a pseudorandom “mixing” function. When creating a new volume, the Random Number Generator generates the master key, secondary key, and the salt.
By default, Passware Kit checks for all possible encryption types. However, if a user knows the exact encryption and hash algorithm, he or she can specify them in the Passware Kit settings:
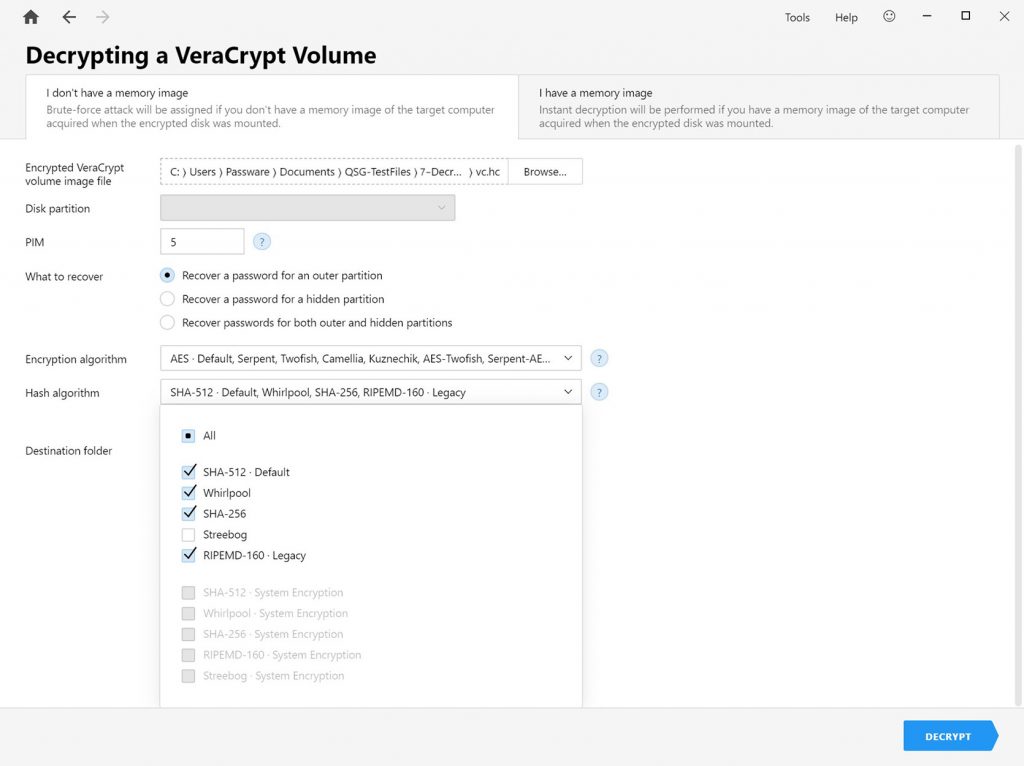
Reducing the number of encryption and hash algorithms to check increases password recovery speed significantly. Starting from version 2022.4, Passware Kit detects VeraCrypt hash types of Windows system volumes with GPT partition tables. This helps to avoid checking irrelevant hashes and significantly speeds up the overall VeraCrypt password recovery process.
Users can also narrow down the number of hashes to check if they know the version of VeraCrypt used for encryption. For example, VeraCrypt supports the Ripemd160 hash. But this hash is not available for encryption in the latest versions of VeraCrypt, although VeraCrypt supports it for decryption. This condition means that if you know that the container was created with the latest version of VeraCrypt, disable the Ripemd160 checkbox in the Passware Kit settings. Such hashes are marked as “Legacy” in the Passware Kit list. Please note that Passware Kit supports containers created with TrueCrypt version 6 and higher, i.e., it does not support legacy hashes like SHA-1 and encryption type LRW.
The more encryption algorithms used, the longer a cascade becomes. For example, AES-Serpent-Twofish encryption is a triple cascade and it takes three times longer to decrypt than a single cascade. So the user can also reduce decryption time by disabling unnecessary cascades in the Passware Kit settings.
Hidden Partitions
Although Passware Kit is unable to detect whether there is a hidden partition inside the container, it can recover passwords for both outer and hidden partitions, if a user specifies this option.
National Encryption Standards and Default Settings
TrueCrypt volumes can be encrypted using the following algorithms:
- AES, Serpent, Twofish, AES-Twofish, AES-Twofish-Serpent, Serpent-AES, Serpent-Twofish-AES, and Twofish-Serpent.
In addition to these algorithms, VeraCrypt supports the following encryption types:
- Camellia, Kuznyechik, Camellia-Kuznyechik, Camellia-Serpent, Kuznyechik-AES, Kuznyechik-Serpent-Camellia, and Kuznyechik-Twofish.
Knowing the national encryption standards of a particular country can reduce the decryption options in Passware Kit, thus reducing time spent on password recovery.
For example, the US National Security Agency has approved the AES/SHA hash to satisfy Information Assurance requirements associated with the protection of national security systems and/or national security information.
If nothing is known about the encryption type, choose the one used in the TrueCrypt/VeraCrypt application by default:
- TrueCrypt: hash Ripemd160, cascade AES
- VeraCrypt: hash SHA-512, cascade AES.
PIM
Prior to version 1.12, the security of a VeraCrypt volume was only based on the password strength because VeraCrypt used a fixed number of iterations. With the introduction of PIM (Personal Iterations Multiplier), VeraCrypt has a 2-dimensional security space for volumes based on the couple (Password, PIM).
The PIM can be specified in Passware Kit settings. In general, the larger the PIM, the more iterations are applied to encryption, i.e., the slower the password recovery process is.
If no PIM is specified, Passware Kit uses the default value for each hash type, e.g.:
Ripemd160: 640...641Ripemd160 System: 159...160Sha256: 485Sha256 System: 97...98Sha512: 485Whirlpool: 485Streebog512: 485Streebog512 Gpt System: 97...98
For short passwords, 19 characters or less, the minimum PIM value is 98 for system encryption and 485 for non-system encryption and file containers. For passwords over 20 characters, the minimum PIM value is 1.
If no PIM value is specified or PIM is specified as 0, Passware Kit uses the default number of VeraCrypt iterations.
Starting from Passware Kit 2023 v2, there is also an option to select a range or set of PIM values to check. Passware Kit then brute-forces the PIMs alongside with the VeraCrypt password.
Acceleration of Password Recovery
When talking about TrueCrypt/VeraCrypt password recovery, the following parameters can affect the speed of the process:
- hash type – the slowest hash type is Streebog,
- PIM,
- cascade length (although the type of cascade does not affect the recovery speed).
Password recovery speed for TrueCrypt/VeraCrypt can be accelerated with GPU, as well as cloud services (e.g., Amazon) and distributed computing. For TrueCrypt system volumes with a 1-cascade encryption, the speed on an NVIDIA RTX 2080 Ti is 1,050,000 passwords per second. Decryptum Password Recovery (DPR) works with this type of encryption at the pace of 10,000,000 passwords per second. For VeraCrypt volumes, the recovery speed on DPR is significantly lower: about 35,000 passwords per second on a 1-cascade encryption with the default PIM.
Please note that for TrueCrypt/VeraCrypt password recovery, it takes a bit longer (up to ten minutes) to calibrate the GPUs than for other file types.
Summary
The key is to detect whether the volume is TrueCrypt or VeraCrypt. Check the suspect’s computer registry and drivers installed. Once the proper application is identified, speed up the password recovery process by disabling the irrelevant types of encryption, hash algorithms, and PIM in Passware Kit settings. And of course, apply hardware acceleration in accordance with your budget and availability in your network environment. TrueCrypt/VeraCrypt password recovery is time-consuming, but knowing the aspects of encryption will increase your chances of getting the password in a reasonable time.