Table of Сontents
- A Bit of History
- Apple File Systems
- Software and Hardware Levels
- Decrypting FileVault2 volumes from Macs without T2/M1/M2/M3 chips
- Decrypting FileVault2 volumes from Macs with a T2 chip
While Apple’s commitment to user privacy and security remains their priority, the field of computer forensics faces a solid challenge when it comes to extracting evidence from encrypted Apple devices.
This article provides comprehensive insights into Apple’s native encryption, covering both software and hardware-based levels.
A Bit of History
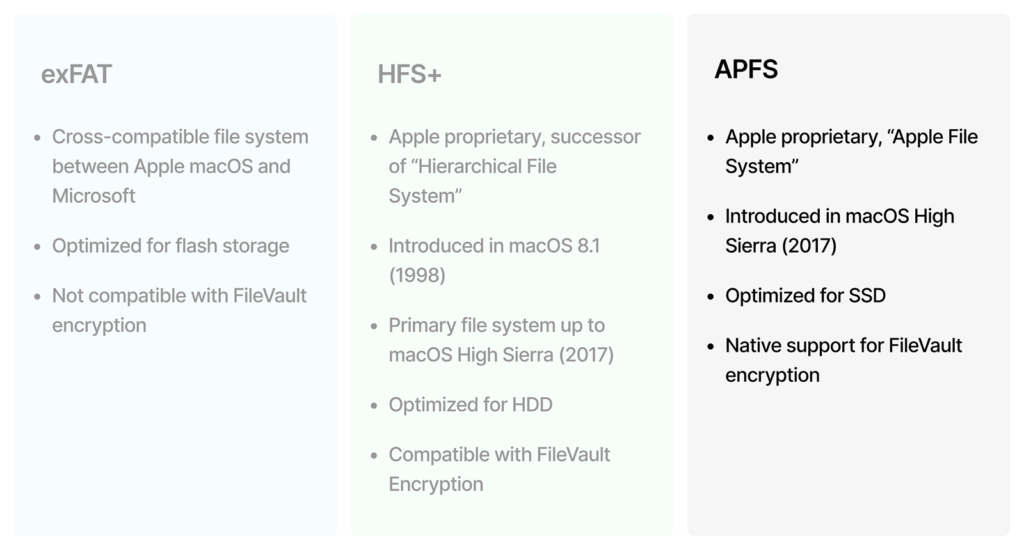
Apple supports the following file systems: FAT, exFAT, HFS+, and APFS. HFS+ is an Apple proprietary file system and the successor of HFS, or Hierarchical File System. HFS+ was first introduced in macOS 8.1 in 1998 and was the primary file system for Mac devices and early iPhones until the introduction of APFS in macOS High Sierra in 2017. HFS+ is compatible with FileVault and FileVault2.
APFS, which stands for Apple File System, is the latest Apple proprietary file system. It was introduced in 2017 in macOS High Sierra and is optimized for SSD storage. Unlike HFS+, APFS on Macs has native support for FileVault2 single-key encryption, where the same key is used across the entire disk.
Software and Hardware Levels
Native encryption of Apple devices comprise software level, i.e., FileVault and FileVault2, and hardware level, i.e., T2, M1, M2, and M3 chips.
FileVault is a legacy system introduced in 2003 with macOS Panther, which allows one to encrypt a home user directory only. FileVault2 was introduced in 2011 with macOS X Lion and allows one to encrypt the entire disk. It uses a 256-bit AES encryption and allows one to set a system start-up password.
The T2 Security chip, a new layer of encryption introduced in 2017, provides encryption services and secure boot for iMac, Macbook Pro, Mac Mini, and other devices. Macs with T2 chip may or may not be protected with FileVault2 software-level encryption. It is impossible to acquire an image of a T2-protected FileVault2 disk by simply removing the storage; moreover, the T2 prevents users from booting into a forensic environment. However, it is possible to use Passware Kit to obtain read-only access to such Macs using the Target Disk Mode or even brute-force the original user password.
Hardware encryption on the latest Macs is performed by M1-M3 chips, which are not yet supported by any existing forensic software products.
Decryption
There are several approaches to handling native Apple encryption. In addition to decrypting the FileVault2 volume, Passware Kit also decrypts and creates an image of the unallocated volume data that may contain deleted data. This data can be of particular importance in discovering electronic evidence.
Decrypting FileVault2 volumes from Macs without T2/M1/M2/M3 chips
1. Instant decryption via memory analysis
If there is a memory image acquired when the encrypted disk was mounted, it can be used to extract the encryption key and thus decrypt the volume without brute-forcing the password. Passware Kit Ultimate includes a Bootable Memory Imager that allows one to dump the Mac memory image in a forensically-sound way.
2. Instant decryption using the recovery key
Passware Kit can instantly decrypt the FileVault2 volume by extracting the recovery key from an Apple Keychain or iOS backup. A decrypted Keychain file from one device can be used to decrypt or unlock the APFS volume of the same iCloud account. The recovery key required for the decryption presents in the decrypted Keychain if the “save the FileVault2 recovery key to the iCloud” option was checked during the FileVault2 initialization.
Both Mac Keychain and iOS Keychain can be decrypted using Passware Kit Ultimate. Passware Kit can also recover the iOS backup password if it is unknown, which helps to extract the keychain.
3. GPU-accelerated brute-force password recovery
This is the most time-consuming approach. However, as there may be multiple Mac users that have permission to unlock the disk, the chances of recovering the password for at least any of them are higher. Also, Passware Kit instantly extracts and displays password hints for FileVault2 accounts, which might be extremely helpful in guessing the passwords.
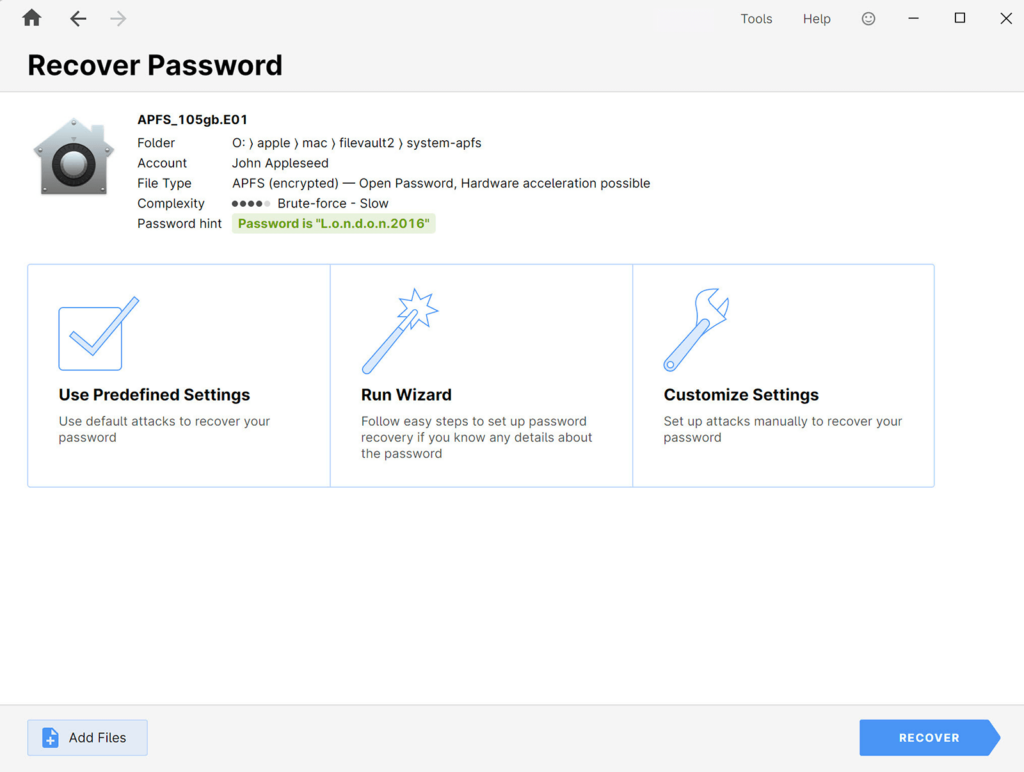
For disks encrypted on the HFS+ file system, Passware Kit requires a FileVault Wipekey file to perform the password recovery. The Wipekey can be specified by user or Passware Kit attempts to detect it automatically on the default location.
Passware Kit accelerates the password recovery process using GPU and distributed computing. The average performance is over 80,500 passwords per second on NVIDIA GeForce RTX 4090.
Decrypting FileVault2 volumes from Macs with a T2 chip
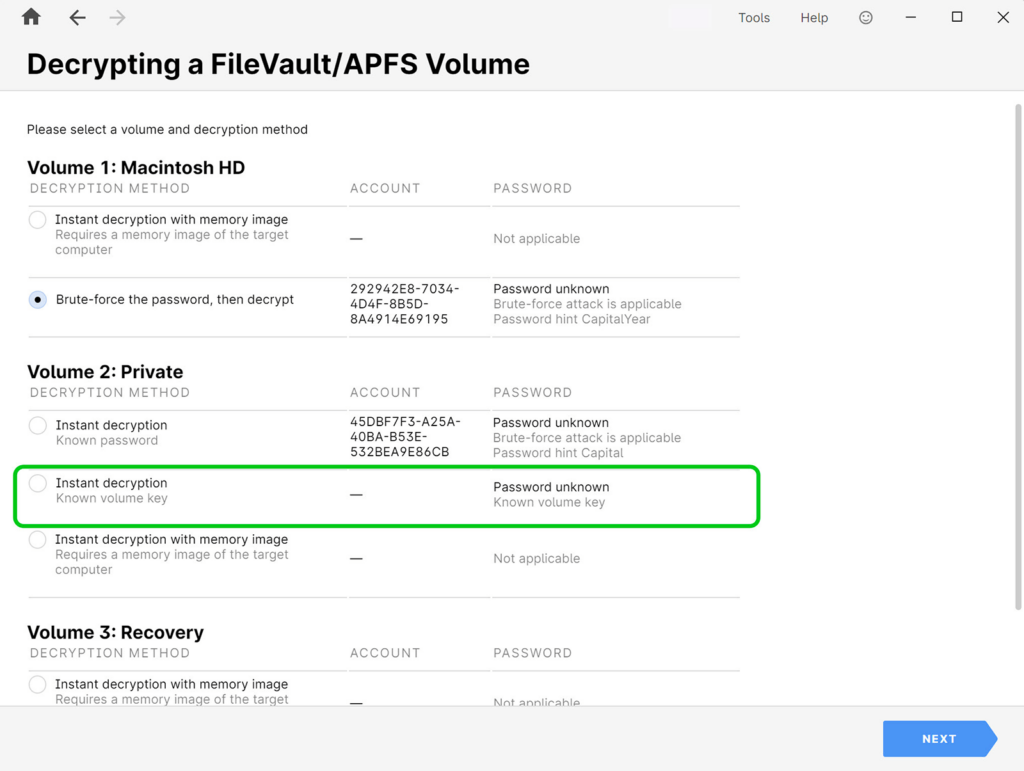
1. Instant decryption using the volume key
The APFS T2-protected drive may be encrypted with just a hardware key, which is not linked with a user password, i.e., when the FileVault2 is disabled. In this case, Passware Kit Ultimate instantly recovers the hardware key and decrypts the encrypted volume. In some cases, this key can instantly provide access to other volumes of the same APFS container using the “Known volume key” decryption method in Passware Kit:
2. Getting the read-only access (unlock) to the target disk
A T2 chip decrypts data from the drive on the fly. The encryption keys are unique and cannot be extracted in any way, so the only solution to reading the device data is to bypass the T2 chip. This is possible by booting the target machine into the Target Disk Mode (holding the ‘T’ key while booting until it enters the target disk mode). Forensic specialists can then connect the Mac running Passware Kit to the target Mac using a thunderbolt cable and following the Passware Kit onscreen instructions; the target Mac will then display its storage in read-only mode.
The FileVault2 software-level encryption should be removed at the same time. In order to do this, Passware Kit requires a recovery key extracted from either an unlocked iOS backup or a decrypted keychain from any device of the same iCloud account.
3. Brute-force password recovery with Passware Kit Ultimate
More information is available to forensic examiners by request.
Summary
Here are some use-cases that describe the decryption options in more detail.
In all the above cases, forensic examiners must work with APFS disk images, both for brute-force password recovery and decryption. An EFI (firmware) password, which can differ from the macOS user password, prevents Mac from loading in Target Disk Mode, thus preventing image acquisition.
Passware Kit Ultimate includes an option to recover the Mac EFI password, regardless of the presence of a T2 chip, or to instantly remove it for Macs without T2. A restore option is also available, which allows users to reset the previously removed password.
Read the full article, including the summary of Passware Kit capabilities to handle Apple encryption, on the Passware Knowledge Base.